|
Try the below script in the AT Command Tester tool
// //Script: at!udusbcomp.at //This AT command is used to set the USB interface configuration the Sierra Wireless modules. //Enter the password AT!ENTERCND="1234" WAIT=1 //Query the at!udusbcomp support AT!UDUSBCOMP=? WAIT=1 //Get the current USB interface of the Sierra Wireless modem AT!UDUSBCOMP? WAIT=1 //Set the USB interface AT!UDUSBCOMP=7
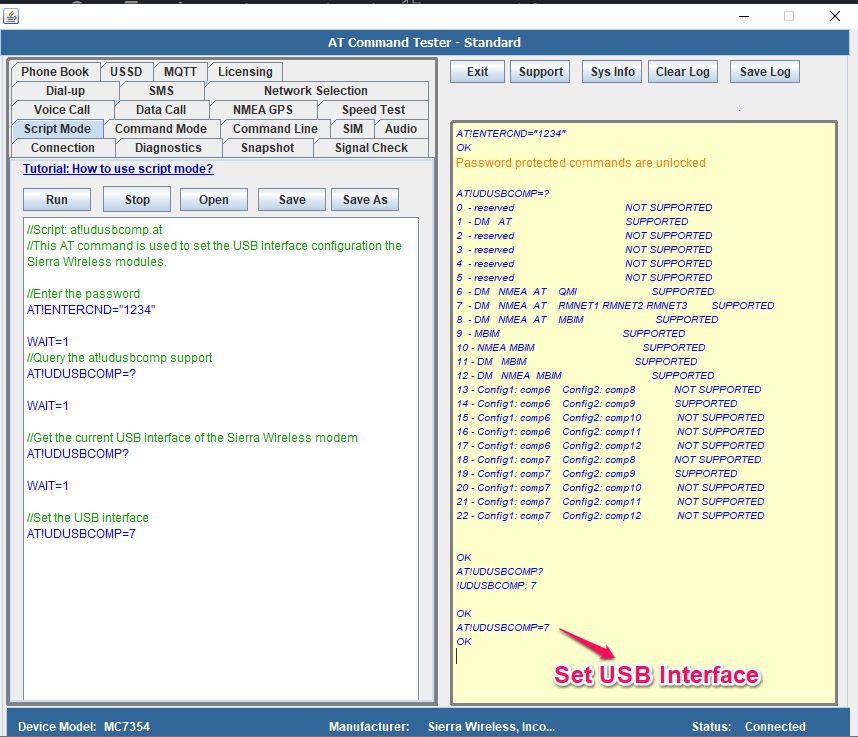
Output of the above script in the AT Command Tester tool
AT!ENTERCND="1234" OK Password protected commands are unlocked AT!UDUSBCOMP=? 0 - reserved NOT SUPPORTED 1 - DM AT SUPPORTED 2 - reserved NOT SUPPORTED 3 - reserved NOT SUPPORTED 4 - reserved NOT SUPPORTED 5 - reserved NOT SUPPORTED 6 - DM NMEA AT QMI SUPPORTED 7 - DM NMEA AT RMNET1 RMNET2 RMNET3 SUPPORTED 8 - DM NMEA AT MBIM SUPPORTED 9 - MBIM SUPPORTED 10 - NMEA MBIM SUPPORTED 11 - DM MBIM SUPPORTED 12 - DM NMEA MBIM SUPPORTED 13 - Config1: comp6 Config2: comp8 NOT SUPPORTED 14 - Config1: comp6 Config2: comp9 SUPPORTED 15 - Config1: comp6 Config2: comp10 NOT SUPPORTED 16 - Config1: comp6 Config2: comp11 NOT SUPPORTED 17 - Config1: comp6 Config2: comp12 NOT SUPPORTED 18 - Config1: comp7 Config2: comp8 NOT SUPPORTED 19 - Config1: comp7 Config2: comp9 SUPPORTED 20 - Config1: comp7 Config2: comp10 NOT SUPPORTED 21 - Config1: comp7 Config2: comp11 NOT SUPPORTED 22 - Config1: comp7 Config2: comp12 NOT SUPPORTED OK AT!UDUSBCOMP? !UDUSBCOMP: 7 OK AT!UDUSBCOMP=7 OK